10+ dfd threat modeling
Washoe County Arrests MugshotsThis is a Nevada form and can be use in Washoe County The information on this web site is provided to assist users in obtaining information about county jail arrests The death toll from COVID-19 in Washoe County reached 600 over the weekend on Saturday when three new deaths were tallied Its the fourth confirmed case of travel. An ER model is a high- level description of the data and the relationships among the.
Magic Transit Noise
Version 73 was released March 2020.
. Data Flow Diagram of Chat Application 19 27. The Process for Attack Simulation and Threat Analysis PASTA คอ Framework ทใชวเคราะหและประเมนความเสยงของธรกจทมตอ cyber-threat ซง Framework มทงสน 7 step ดงตารางทแสดงตอไปน. EST is proud to announce the winners of the 2021 EST Reviewer Awards from the outstanding team of reviewers who support the journal in the peer review process.
Second Level DFD 38. 目录1资产识别见1532威胁情景识别见1543影响评级见1554攻击路径分析见1565攻击可行性评级见1576风险值确定见1587风险处理决策见159概述 本条款描述了确定道路使用者受威胁情景影响程度的方法这些方法及其工作产品统称为威胁分析和风险评估tara从. 37 24 ER DIAGRAM An ER diagram can be used to design logical database schemas.
Déjà plus de 15 millions dutilisateurs. Gratuit et sans pub. It runs only on Windows 10 Anniversary Update or later and so is difficult.
Threat modeling is an integral part of the Security Development Lifecycle. Accounting Information Systems SEVENTH EDITION - Academiaedu. Firmware replacement Updates and patches to devices are usually done remotely.
The trees are presented such that the leaf. The GUI Operates in two forms Contacts Forms and Chat forms. 36 233 SECOND LEVEL DFD.
For example one threat tree explores how tampering might manifest itself against a data flow in a general sense. 210 METHODOLOGY 2101 Project Summary The user interacts with the tool using GUI. MDR provides security monitoring using real-time threat intel and Security Orchestration Automation and Response SOAR.
Avec FamilyAlbum partagez en privé et sauvegardez en illimité les photos et vidéos des enfants. 2006 in which threat trees are developed for STRIDE threats against each of the four standard DFD elements. Some of the most popular local exploits targeted by threat actors are as follows.
29 Data Flow Diagram Figure 10. If the process is not secure threat actors could intercept the update and install their own malicious update in which case they could have full control over the device and begin attacking other. Our thanks and appreciation goes out to this global team of loyal dedicated and talented reviewers who perform this vital role and uphold the high quality science EST is committed to publishing.
It is one of the longest lived threat modeling tools having been introduced as Microsoft SDL in 2008 and is actively supported. The Microsoft Threat Modeling Tool TMT helps find threats in the design phase of software projects. This scalable threat monitoring service enables all Continental United States CONUS government entities trusted and reliable cyber defense at a fraction of the cost of traditional 247 in-house incident response programs.
Second level DFD shows the whole fact that happen in the system and its given below. First Level DFD 37.
What Is Threat Modeling All You Need To Know Overview

Uml Component Diagram Example Online Shopping Uml Collaboration Diagram Uml2 0 Uml Class Diagram Example Apartment Plan Deployment Diagram For Online Bookstore In Uml

20 Flow Chart Templates Design Tips And Examples Venngage
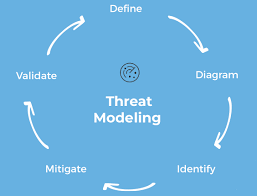
What Is Threat Modeling All You Need To Know Overview

What Is Threat Modeling All You Need To Know Overview

20 Flow Chart Templates Design Tips And Examples Venngage
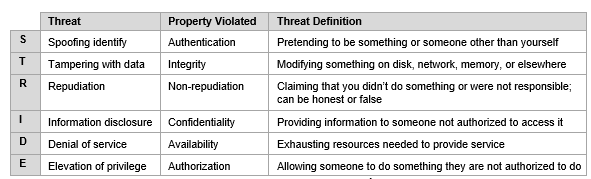
What Is Threat Modeling All You Need To Know Overview

20 Flow Chart Templates Design Tips And Examples Venngage

Threat Modelling An Overview Knoldus Blogs

Pdf Security Risk Management In E Commerce Systems A Threat Driven Approach
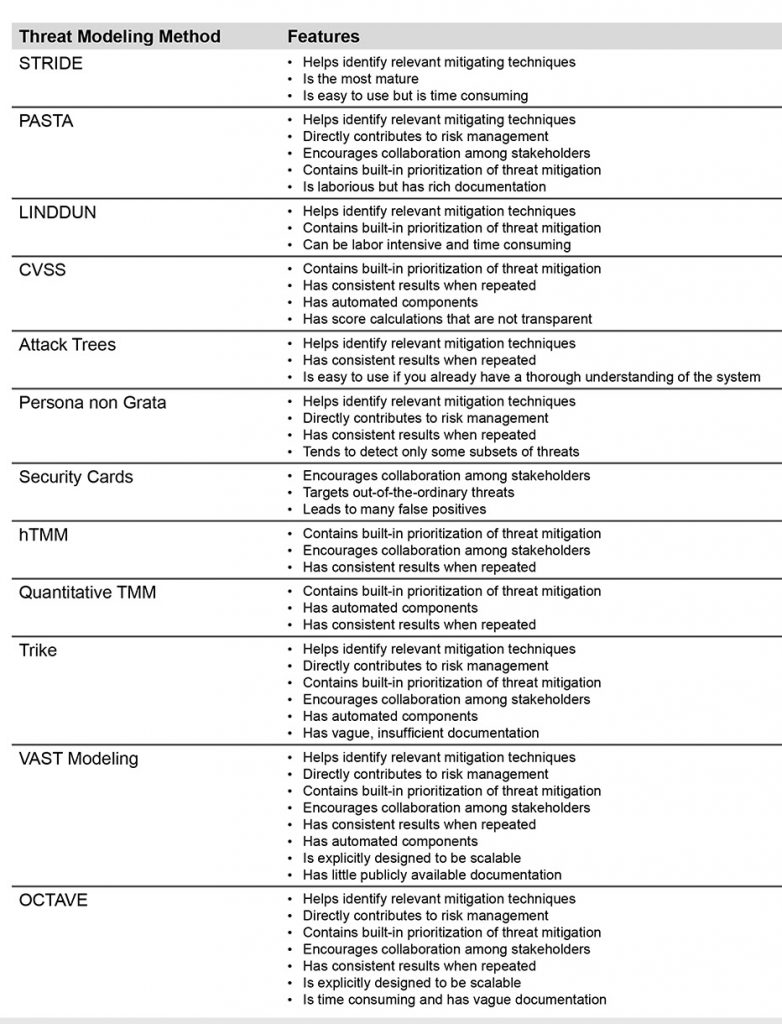
What Is Threat Modeling All You Need To Know Overview
1
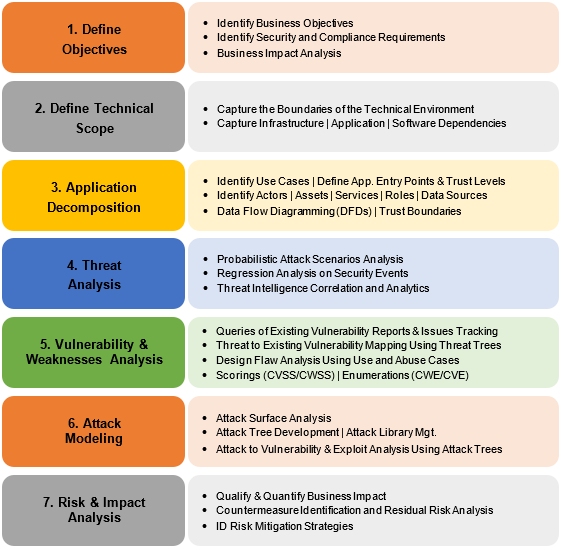
What Is Threat Modeling All You Need To Know Overview

Hardware Platform Interface Wikiwand
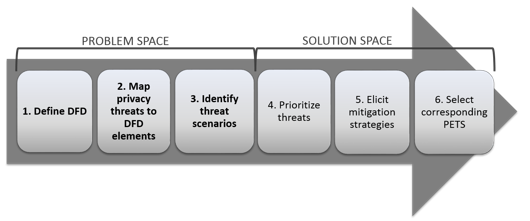
What Is Threat Modeling All You Need To Know Overview

20 Flow Chart Templates Design Tips And Examples Venngage

Threat Model Wikiwand